this post was submitted on 29 Jun 2023
207 points (100.0% liked)
Technology
37746 readers
47 users here now
A nice place to discuss rumors, happenings, innovations, and challenges in the technology sphere. We also welcome discussions on the intersections of technology and society. If it’s technological news or discussion of technology, it probably belongs here.
Remember the overriding ethos on Beehaw: Be(e) Nice. Each user you encounter here is a person, and should be treated with kindness (even if they’re wrong, or use a Linux distro you don’t like). Personal attacks will not be tolerated.
Subcommunities on Beehaw:
This community's icon was made by Aaron Schneider, under the CC-BY-NC-SA 4.0 license.
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
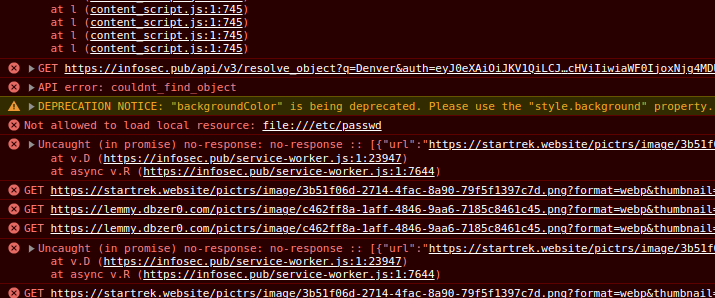
Holy shit this is kind of unsettling. Though I would expect ALL major browsers to reject reading any local files like this..... would this kind of thing actually succeed somewhere/somehow?
If you ran your browser as root and configured your browser to load local resources on non-local domains maybe. I think you can do that in chrome://flags but you have to explicitly list the domains allowed to do it.
I'm hoping this is just a bad joke.
Yeah, seems highly unlikely to ever yield any results. Even if you did manage to read a file, you have to get lucky finding a password hash in a rainbow table or the password being shit enough to crack.
Also generally the actual password (or rather its hash) is stored in /etc/shadow on most systems from the past 20 odd years.
Yeah this is a TIL for me. I didn't realize they were separated out. It makes sense, though I grant I've never taken a close look at these files.
And if anybody has publicly accessible ssh on their desktop machine, that allows password login, they're kinda asking for it.
I cracked the BMC on my workstation motherboard by binwalking the publicly available firmware and finding, to my delight and dread, that the built in root user password was laughably weak. If a top5 motherboard manufacturer is still doing shit like that, users are too.
I also work in support and have seen first hand the bananas things people do, even smart people that should know better